Image Signing (and verification)
So far, we have made sure that we’re only building from signed commits, using Trusted Artifact Signer’s keyless signing capabilities.
But what of our images? When we build an image, we want to sign it, so we’re able to verify its integrity and authenticity before we deploy it.
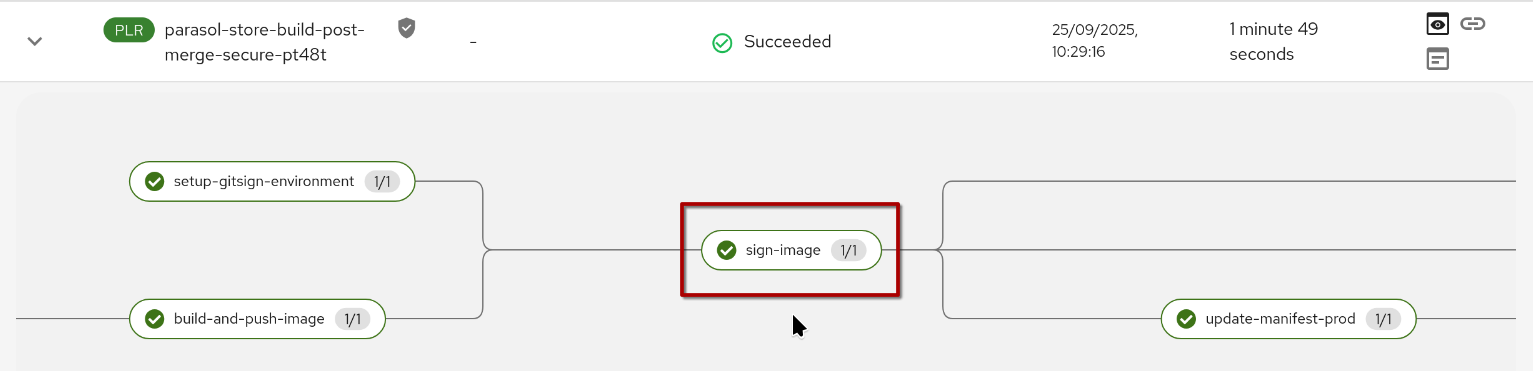
The post-merge pipeline
In our scenario (yours might look different), the pre-merge pipeline is building an image to prove it can be built, but the generated image tag will not be deployed anywhere.
The image generated in our post-merge pipeline is the one that will be deployed (using a GitOps approach) to higher-level stages. Therefore, we should add image signing to this pipeline.
Since we already changed the post-merge pipeline to a security-augmented version, we are now also signing the created image using Trusted Artifact Signer:
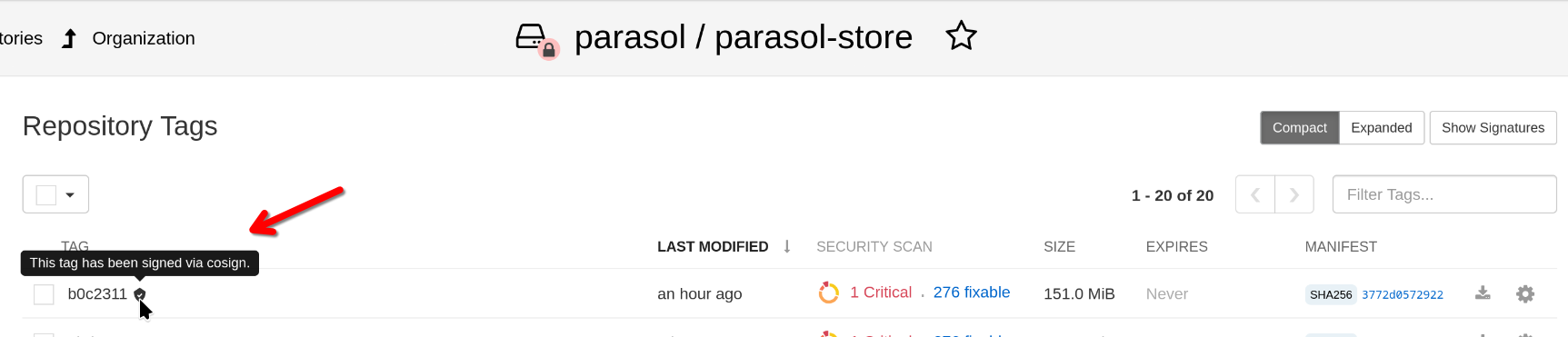
How is this done? Since a pipeline task cannot authenticate via a browser…
If you look at the signing task in the pipeline, you can see that we are getting an OIDC token for a "Pipeline User" - and this token is (along with a number of endpoints) stored as environment variable - and this is what cosign (the signing CLI) uses.
Therefore, the actual signing task is as simple as
cosign sign $(params.IMAGE)When you open the Parasol Quay Repository, you can see that Quay recognises the signature:
And similarly to our commit signing exercise, we have an entry in the Rekor Transparency Database
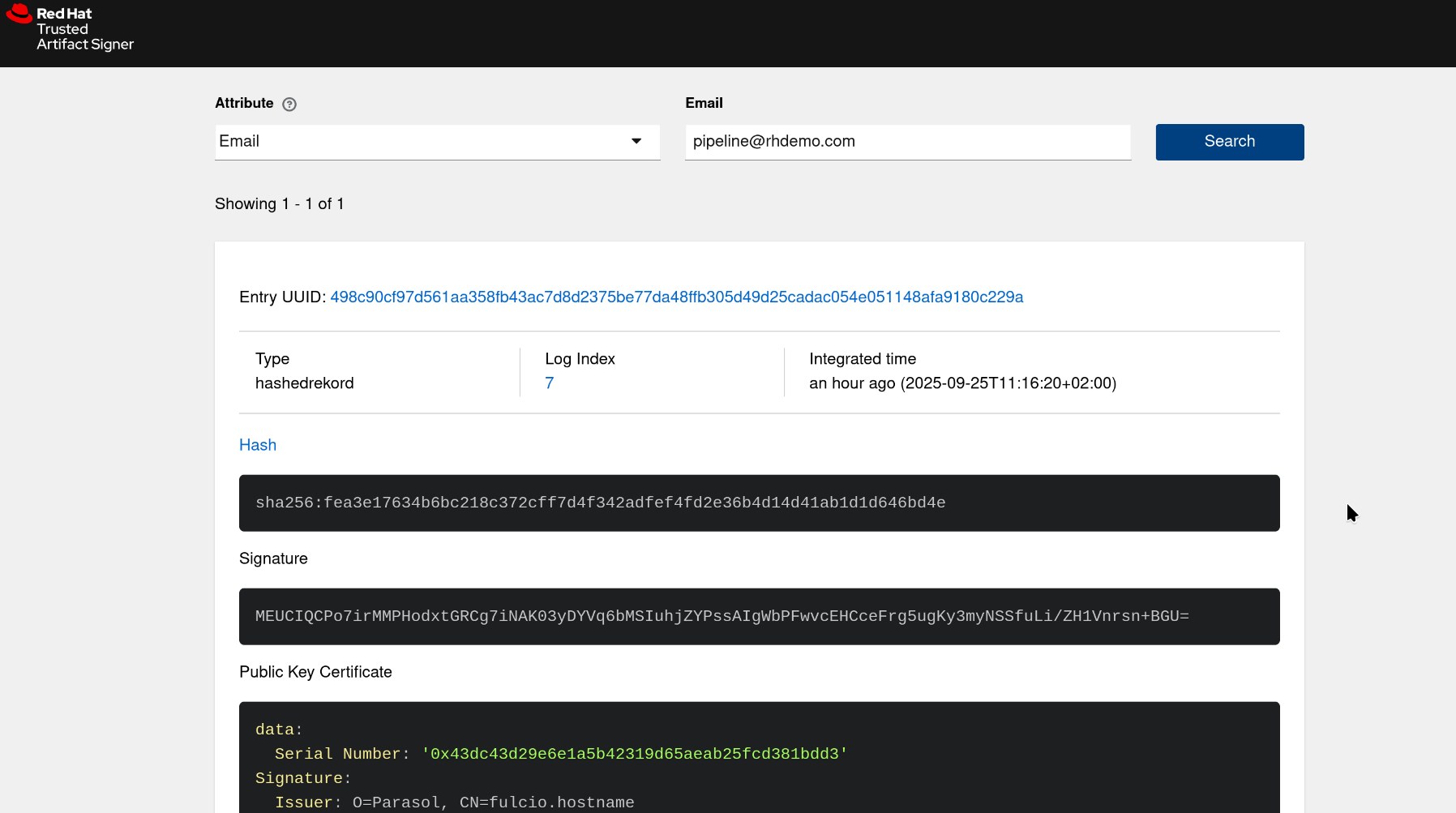
Given this flexibility, we can e.g. sign different pipelines with different users and later validate where the artifact came from, who signed it and when.